PicoGlitcher PCB
A dirt chip fault-injection device
I am selling the PicoGlitcher on faultyhardware.de.
More links:
- The Pico Glitcher and findus (the software to control the Pico Glitcher) are open source: fault-injection-library
- Documentation of the Pico Glitcher and findus: fault-injection-library.readthedocs.io
- hackaday.io project page: hackaday.io/project/196357-picoglitcher
- The Pico Glitcher was featured on Hackaday: hackaday.com/2024/10/30/use-picoglitcher-for-voltage-glitching-attacks/
Update: Many thanks to Troed Sångberg who successfully built a PicoGlitcher. For his built, he made a parts list on Mouser which you can find here.
This project is intended to make fault injection attacks against microcontrollers accessible for hobbyists and to introduce the topic of voltage glitching. The software offers an easy entry point to carry out your own attacks against microcontrollers, SoCs and CPUs. With the provided and easy to use functions and classes, fault injection projects can be realized quickly.
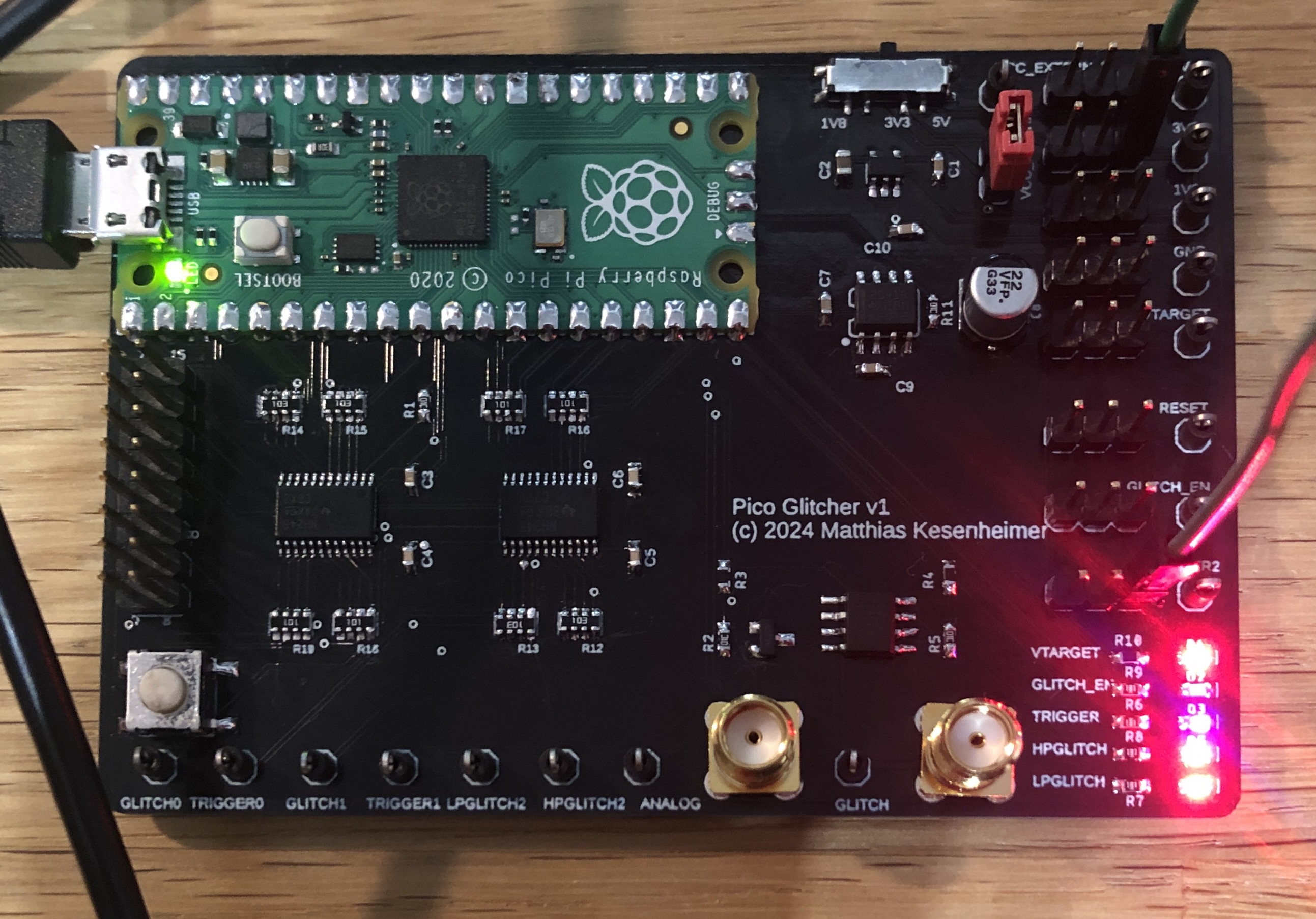
Voltage glitching attacks are usually done with expensive hardware such as the ChipWhisperer Pro or Husky. However, for most of the attacks a Raspberry Pi Pico and a few other components are required. In order to achieve the best results, a circuit board was developed to combine the best of both worlds: cheap, easy to use and powerful.
Introduction
Voltage glitching attacks are a class of hardware attacks that exploit the vulnerability of electronic systems to sudden and brief changes in their power supply voltage. By intentionally introducing these abrupt voltage changes, or "glitches," attackers aim to disrupt the normal operation of the target device, causing it to malfunction in a controlled manner. This can result in the bypassing of security measures, corruption of data, or unintended execution of code. Voltage glitching is particularly relevant in the context of embedded systems, such as microcontrollers and smart cards, which are commonly used in secure applications including payment systems, access controls, and IoT devices.
The core concept behind voltage glitching is to induce faults at precise moments during the execution of critical operations within the device. These faults can lead to outcomes such as skipping security checks, extracting secret keys, or gaining unauthorized access to protected functions. The success of a voltage glitching attack relies on careful timing and an understanding of the target device's behavior under different power conditions. Attackers often use specialized equipment to generate and control these glitches with high precision, making this technique both sophisticated and powerful.
Previously featured projects
Glitching has been previously described on Hackaday for example here (everything you didn't know you need to know about glitching attacks) or here (Apple Airtags hacked and cloned with voltage glitching). The latter even describes attacking an Apple Airtag with a Raspberry Pi Pico and a mosfet.
Existing hardware
Usually these attacks are carried out by expensive hardware such as the ChipWhisperer Pro, the ChipWhisperer Husky, or the devices from Riscure. As these devices are typically very expensive (several hundred Euros), they are not accessible for the hobby hacker. The ChipWhisperer Husky is even more inaccessible for hobby hackers since it has long shipping times up to several weeks.
The PicoGlitcher
It turns out, however, that voltage glitching attacks can easily be performed with cheap and available hardware like the Rapberry Pi Pico and some other components. The sampling rate of the Raspberry Pi Pico is fast enough to enable attacks against most common microcontrollers like the ESP32 or STM32 processors. To gain more insight into voltage glitching attacks and using only cheap components, the PicoGlitcher was born.
The hardware required for the PicoGlitcher involves, of course, a Raspberry Pi Pico and additional components for precise voltage control and monitoring. Specifically, it includes a power supply capable of switching the target on and off, and crowbar transistors that can switch up to 66 amps. The design of the voltage glitching stage of the PicoGlitcher is exactly the same as found in the ChipWhisperer Pro. Furthermore, the board provides several different voltages to supply all kinds of different target boards. A built-in level shifter translates between the fixed voltages of the Raspberry Pi Pico and the voltage levels of the target board.
Glitches must be placed very precisely. The PicoGlitcher is able to trigger on various external events. For example, a rising or falling edge could be used to start the timers. Additionally, the PicoGlitcher can sniff on a UART communication and trigger if a specific word is sent.
To summarize:
- The PicoGlitcher is cheap (less than 30€) in comparison to professional equipment
- Various trigger capabilities: Rising or falling edge trigger, UART trigger, etc.
- Level shifters to trigger on signals with different voltage level.
- Low and high power crowbar mosfets to switch up to 66 amps.
- SMA connectors for the glitch output and ADC input.
- Trigger Sampling rate up to 125MHz, meaning a glitching resolution under 10ns.
- A software-controllable voltage output. This can be used to supply the target and to switch it on and off if hard errors occur.
- Voltage outputs from 1.8V, 3.3V to 5V.
- Fully customizable and easy to understand software: main language is Python and MicroPython
The Software
The corresponding software, the "fault-injection-library", is a Python library specifically designed to perform fault injection attacks on microcontrollers. To set it up, clone the repository, create a virtual environment, and install the necessary dependencies using pip. The Raspberry Pi Pico is used for executing these attacks, and the required MicroPython scripts must be uploaded to the device. Example scripts for performing attacks and analyzing results are provided, demonstrating how to manipulate target devices by injecting precise voltage glitches.
The fault-injection-library also supports the ChipWhisperer hardware (Pro and Husky). So if you have access to these tools, you can use this library to perform fault injection attacks.
For more details, visit the GitHub page.
September 12 2024: Assembly of the updated PCBs
After ten days I received my order from JLCBCP. As mentioned in the previous project log, generating the design files (gerber, CPL and BOM) was fairly straight forward.
The finished PCBs are of high quality. I could not find any errors and the components are perfectly placed and soldered. I am really happy with the way the PicoGlitcher PCB turned out.
The next step was to solder the rest of the components onto the board. For example, the Raspberry Pi Pico and some other through-hole components have to be soldered by hand. The finished board can be seen below.
The new design also works flawlessly. I could generate reproducible glitches on a STM microcontroller within a few minutes.
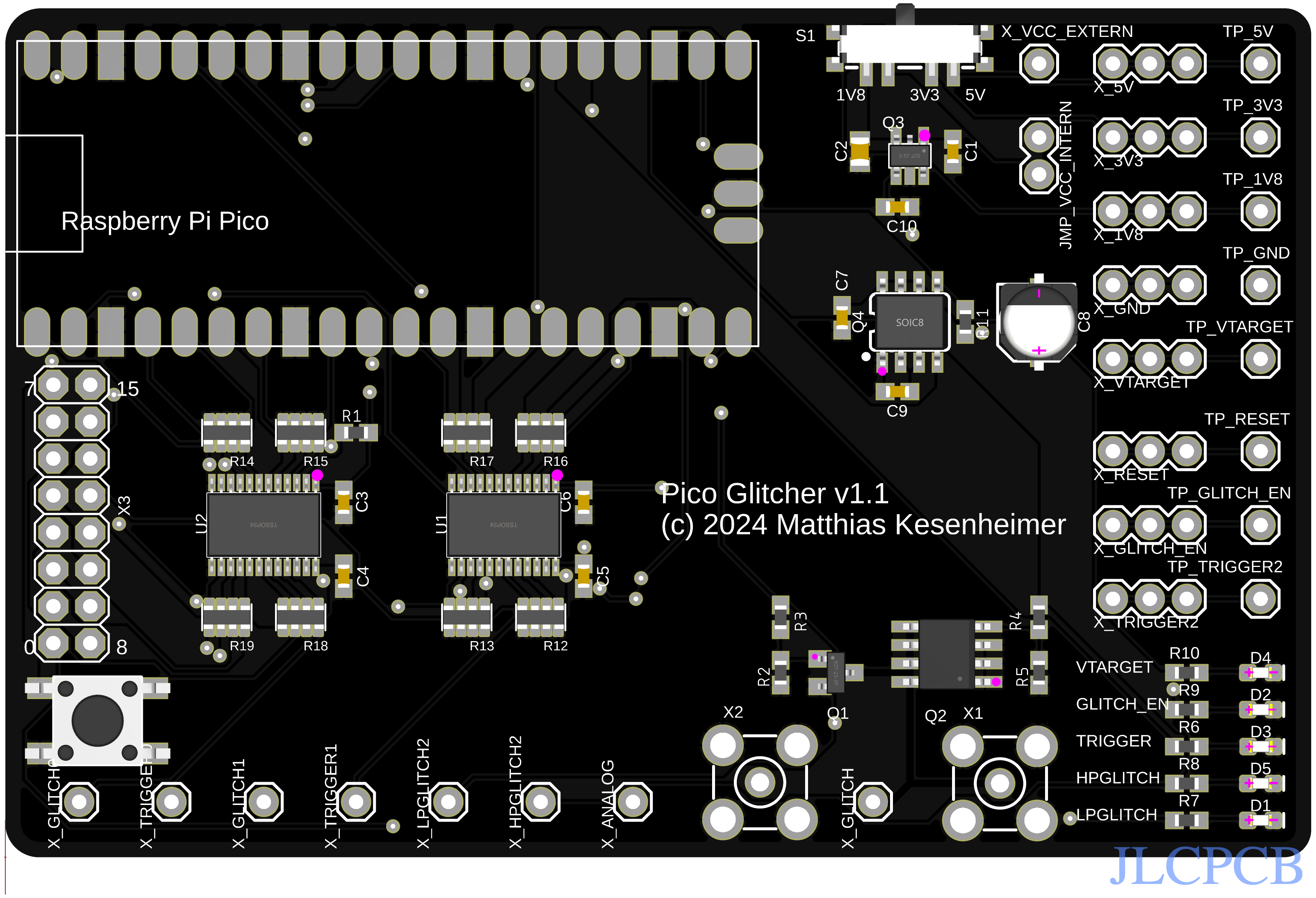
September 3 2024: PCB updates
First of all, the design of the PicoGlitcher is good and I have not found any major flaws yet. The PicoGlitcher works.
However, I have noticed that some of the PCB markings are hard to read, and some are even missing. The component placement is also not optimal, so I decided to update the PCB files. Soldering the small SMD components by hand was difficult (for me at least), so I decided to give PCB manufacturing with component placement a try.
I made a few changes to the design files, picked all the components from JLCPCB via the Assembly Parts Lib and uploaded the new gerber files. In order to automatically generate the BOM and the component placement file (CPL) in Fusion360, I used the library jlcpcb-eagle. With the gerber, the BOM and the CPL files ready, I was finally able to submit my order to JLCPCB. All the relevant files can be found on my github page.
I was surprised at how easy the whole procedure was. The JLCPCB parts library is huge and if an exact part is not available, there is always an alternative. What's more, every step of the process is easy to understand. The component placement is displayed in an online tool that allows you to check that all the components have been placed correctly. Manufacturing and shipping was fast. I received my order within ten days.
Continue reading
Continue reading about the Pico Glitcher and its capabilities, or how to attack various microcontrollers, here:
- The beginning of the Pico Glitcher
- The Pico Glitcher v2
- The Pico Glitcher v3
- Voltage multiplexing and parameter optimization
- Attacking the STM32F4 with the PicoGlitcher
- Attacking the Trezor One Crypto Wallet (new firmware)
- Glitching the Raspberry Pico with a Raspberry Pico
- Attacking the SMT32L051 with the Pico Glitcher
- Attacking the nRF54L15 with an Electromagnetic Fault Injection (EMFI) attack and the Pico Glitcher
- Voltage Glitching with the Pico Glitcher and Findus
- The Pico Glitcher on Youtube